Remote User Authentication Principles|远程用户认证原则
在计算机安全中,用户认证是最基础的构建模块,是防御的第一道防线。In computer security, user authentication is the fundamental building block and the primary line of defense.
用户认证是大多数访问控制和用户责任追踪的基础。User authentication serves as the foundation for most types of access control and user accountability.
根据 RFC 4949 的定义,用户认证是验证一个系统实体声明的身份的过程。According to RFC 4949, user authentication is the process of verifying an identity claimed by or for a system entity.
用户认证的过程包括两步:
身份识别:向安全系统呈现标识符。Identification: Presenting an identifier to the security system.
验证:呈现或生成验证信息,以确认实体与标识符之间的绑定关系。Verification: Presenting or generating authentication information that corroborates the binding between the entity and the identifier.
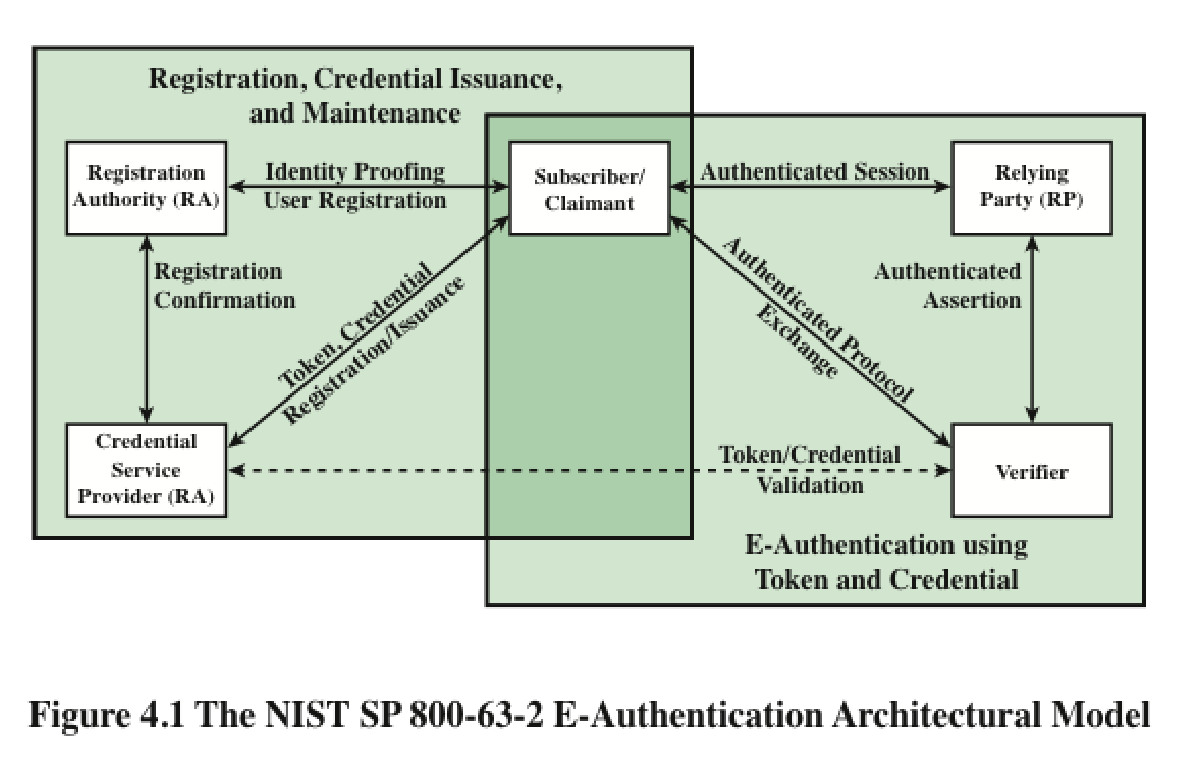
NIST Model for Electronic User Authentication|NIST 电子用户认证模型
NIST SP 800-63-2(《电子认证指南》)定义电子用户认证为建立对通过电子方式呈现给信息系统的用户身份的信任过程。NIST SP 800-63-2 (Electronic Authentication Guideline) defines electronic user authentication as the process of establishing confidence in user identities presented electronically to an information system.
系统可以使用认证后的身份来确定该身份是否被授权执行特定功能。The authenticated identity can be used by the system to determine if the individual is authorized to perform specific functions.
认证和授权功能通常发生在开放网络(如互联网)上,但也可以在局域网等本地网络中进行。Authentication and authorization can occur over an open network such as the internet, or locally over a local area network.
Means of Authentication|认证的方式
用户身份认证通常有四种方式,可以单独使用或组合使用:
There are four general means of authenticating a user’s identity, which can be used alone or in combination:
用户所知的东西(如密码、PIN、预设问题的答案)。
Something the individual knows (e.g., passwords, PINs, answers to prearranged questions).用户拥有的东西(如加密密钥、电子钥匙卡、智能卡、物理钥匙)。
Something the individual possesses (e.g., cryptographic keys, electronic keycards, smart cards, physical keys).用户的静态生物特征(如指纹、视网膜、面部识别)。
Something the individual is (static biometrics) (e.g., fingerprint, retina, face recognition).用户的动态生物特征(如声音模式、手写特征、打字节奏)。
Something the individual does (dynamic biometrics) (e.g., voice pattern, handwriting characteristics, typing rhythm).
Symmetric Key Distribution Using Symmetric Encryption|使用对称加密的密钥分发
对称加密工作需要双方共享相同的密钥,而且该密钥必须受到保护,防止被他人访问。For symmetric encryption to work, both parties must share the same key, and the key must be protected from unauthorized access.
频繁更换密钥有助于限制一旦攻击者获取密钥后能破坏的数据量。Frequent key changes are usually desirable to limit the amount of data that can be compromised if an attacker learns the key.
密钥分发技术。Key distribution technique.
将密钥传递给希望交换数据的两方,而不允许其他人看到密钥的方法。The means of delivering a key to two parties that wish to exchange data, without allowing others to see the key.
Key Distribution Methods|密钥分发方法
对于两个通信方 A 和 B,密钥分发有以下几种方式:
For two parties, A and B, key distribution can occur through the following methods:
由 A 选择密钥并物理传送给 B。
由第三方选择密钥并物理传送给 A 和 B。
如果 A 和 B 曾经使用过密钥,可以使用旧密钥加密新密钥并传送。
如果 A 和 B 各自与第三方 C 有加密连接,C 可通过加密链接将密钥传送给 A 和 B。

Kerberos
Kerberos 是由 MIT 开发的密钥分发与用户认证服务。Kerberos is a key distribution and user authentication service developed at MIT.
它提供一个集中认证服务器,负责对用户与服务器之间以及服务器与用户之间进行认证。It provides a centralized authentication server whose function is to authenticate users to servers and servers to users.
Kerberos 完全依赖对称加密,不使用公钥加密。Kerberos relies exclusively on symmetric encryption and does not use public-key encryption.
Kerberos Version 4|Kerberos 版本 4
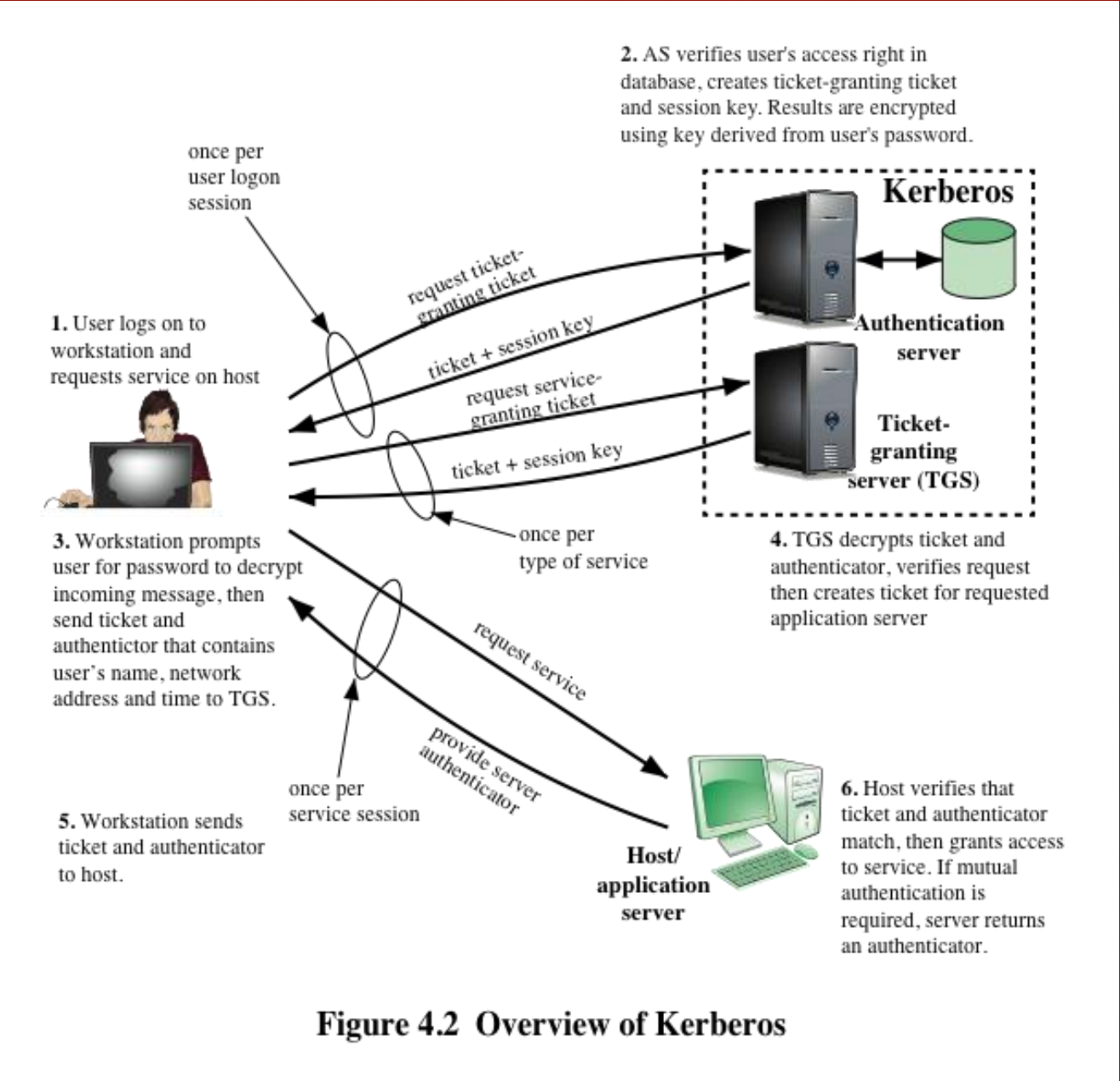
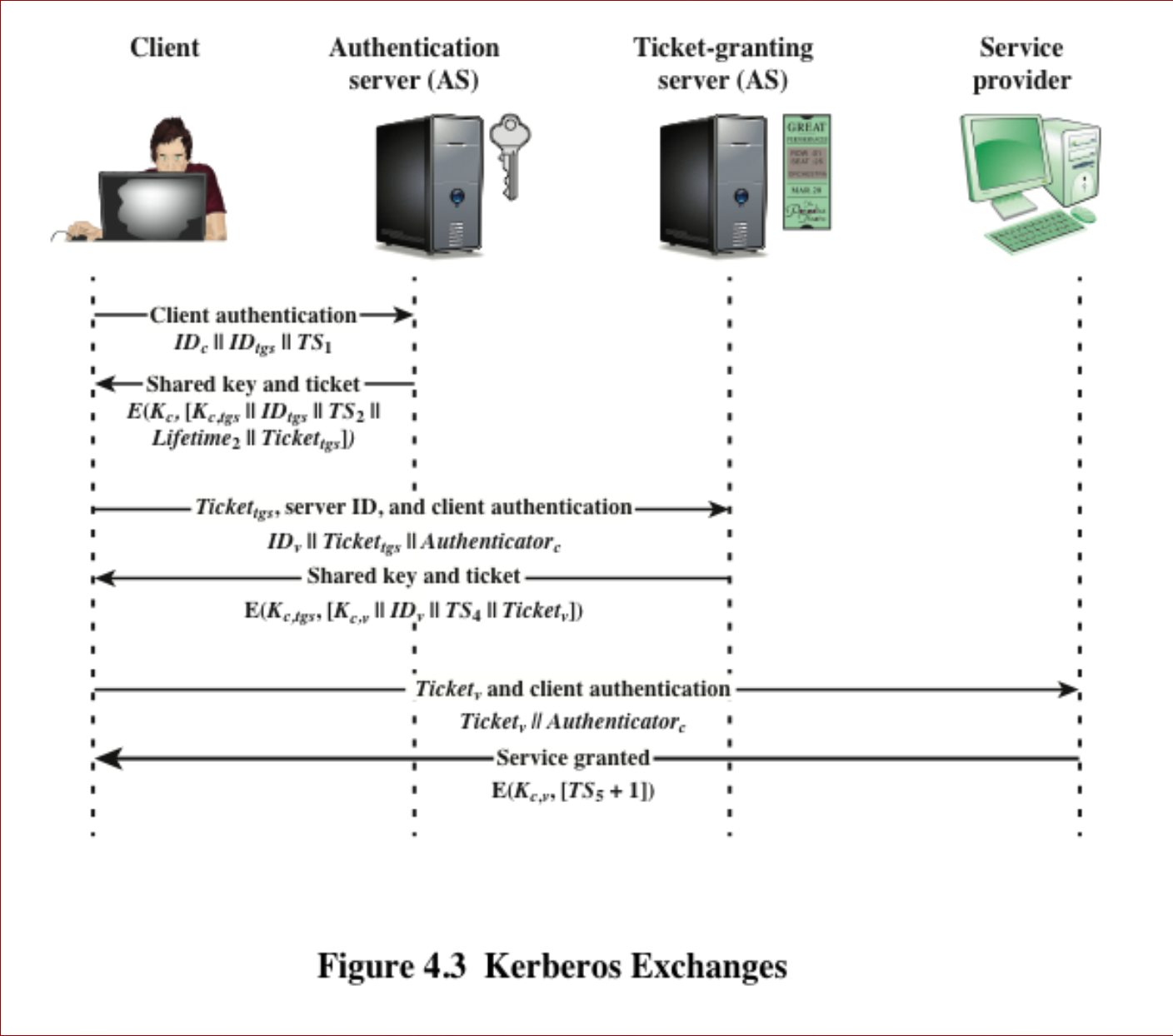
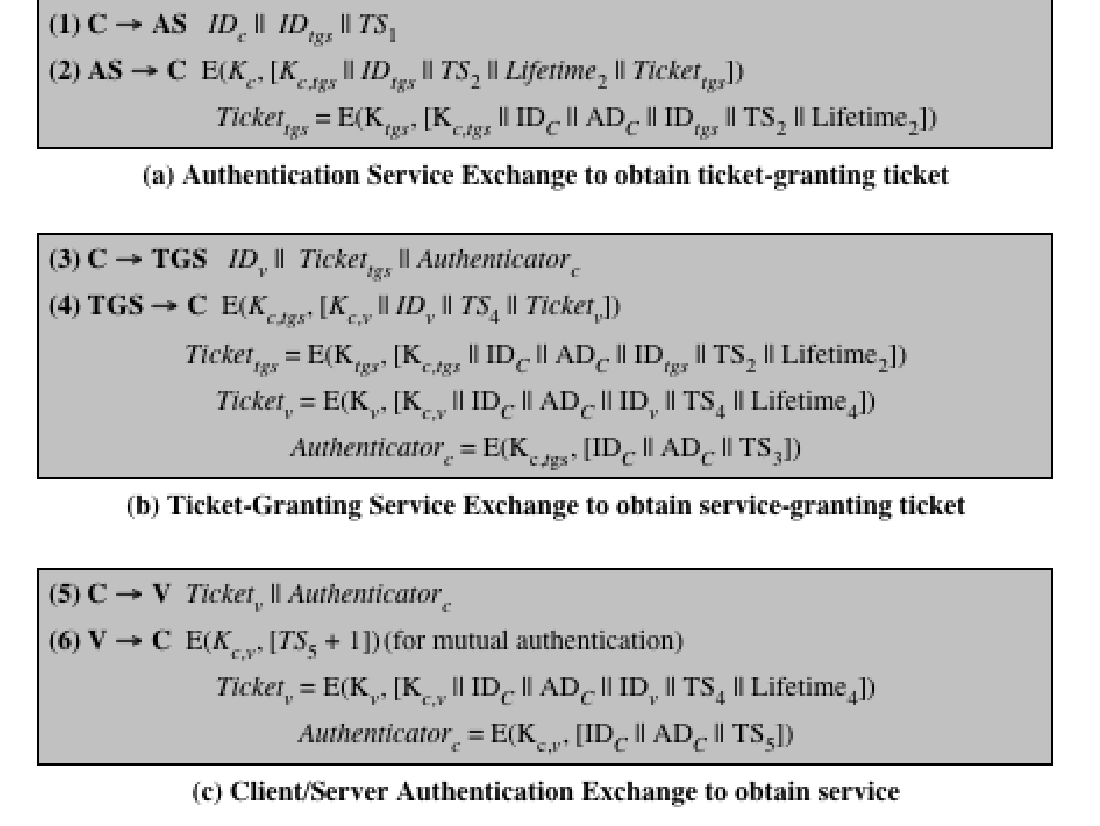
Kerberos 版本 4 是一个基本的第三方认证方案,包含以下关键部分:
Kerberos version 4 is a basic third-party authentication scheme with the following components:
认证服务器(AS):用户与认证服务器协商身份。提供不可损坏的身份验证凭证(票证授予票证 TGT)Authentication Server: Users initially negotiate with AS to identify self. provides a non-corruptible authentication credential(ticket granting ticket TGT).
票证授予服务器(TGS):用户使用认证服务器提供的票证请求访问其他服务。Ticket Granting Server: Users subsequently request access to other services from TGS on basis of users TGT.
版本 4 使用 DES 加密算法。Version 4 uses the DES encryption algorithm.
Kerberos Realms|Kerberos 实例
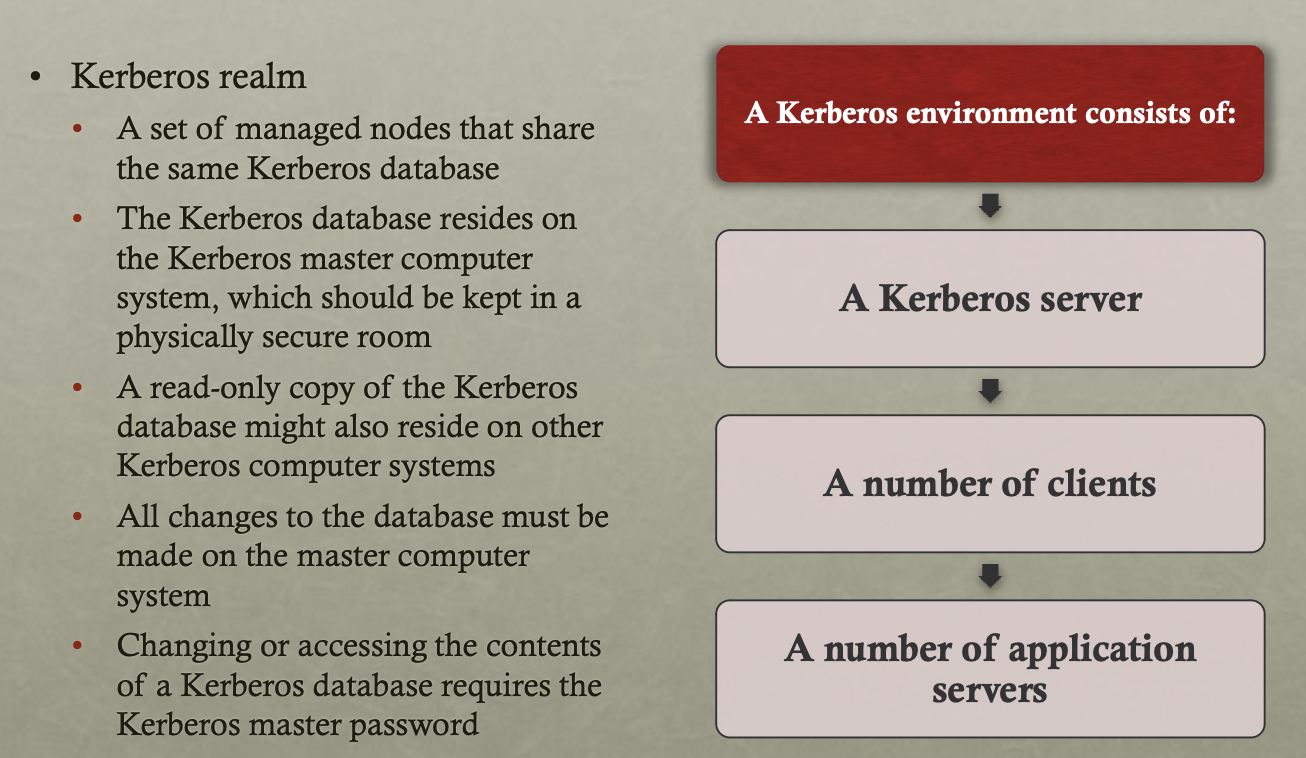
Kerberos 实例是管理节点的集合,共享相同的 Kerberos 数据库。A Kerberos realm is a set of managed nodes that share the same Kerberos database.
所有数据库的更改必须在主计算机系统上进行,访问数据库需要主密码。All changes to the database must be made on the master computer system, and access requires the Kerberos master password.
Kerberos 环境包括:Kerberos 服务器、多个客户端和多个应用服务器。A Kerberos environment consists of a Kerberos server, multiple clients, and multiple application servers.
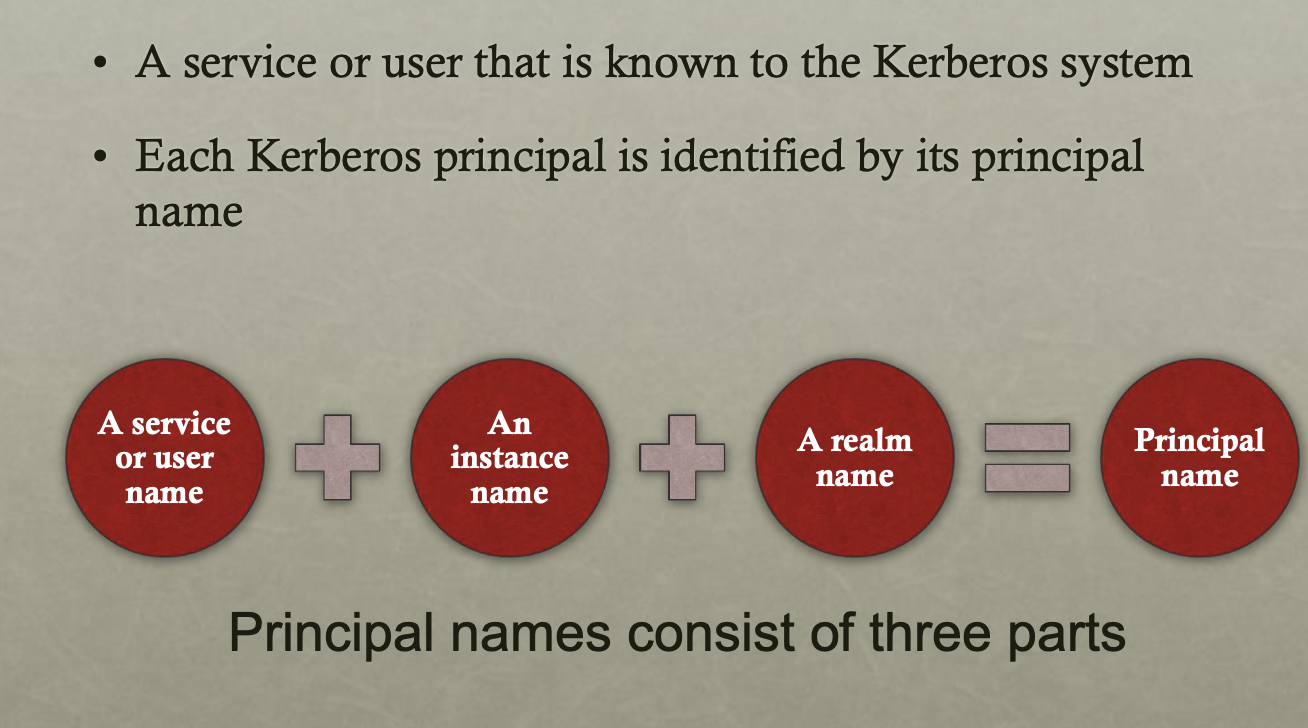
Kerberos Principal|Kerberos 主体
Key Distribution Using Asymmetric Encryption|使用非对称加密的密钥分发
公钥加密的主要角色之一是解决密钥分发问题。One of the major roles of public-key encryption is to address the problem of key distribution.
在这方面,使用公钥加密有两个不同的方面:There are two distinct aspects to the use of public-key encryption in this regard:
公钥的分发 The distribution of public keys
使用公钥加密分发密钥 The use of public-key encryption to distribute secret keys
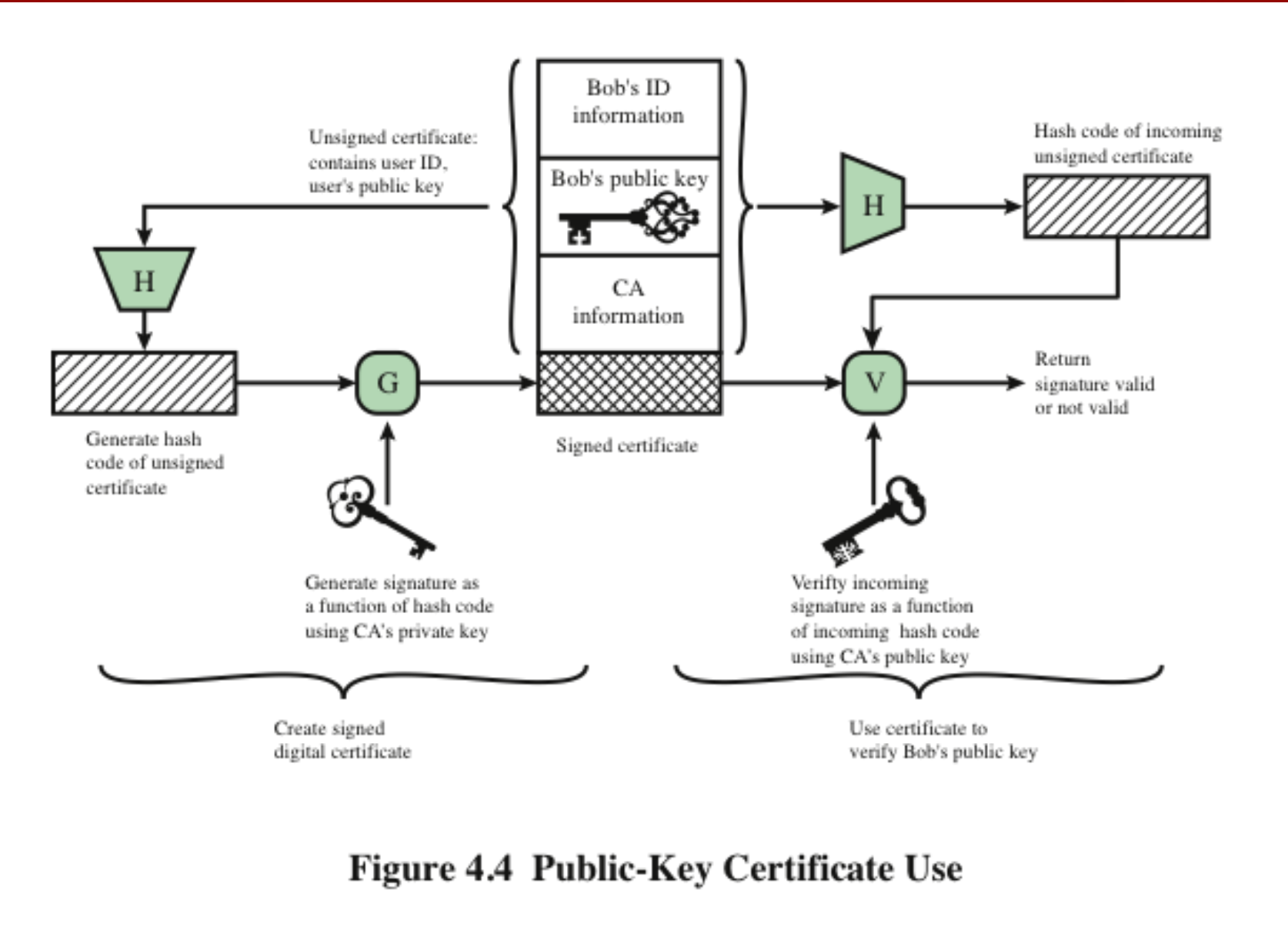
公钥证书 Public-key certificate
由公钥和密钥所有者的用户 ID 组成,整个区块由受信任的第三方签名。 Consists of a public key plus a user ID of the key owner, with the whole block signed by a trusted third party.
通常,第三方是用户社区信任的证书颁发机构 (CA),例如政府机构或金融机构。 Typically, the third party is a certificate authority (CA) that is trusted by the user community, such as a government agency or a financial institution.
用户可以以安全的方式向颁发机构提供他或她的公钥并获取证书。 A user can present his or her public key to the authority in a secure manner and obtain a certificate.
然后,用户可以发布证书。 The user can then publish the certificate.
任何需要此用户的公钥的人都可以获取证书并进行验证。 Anyone needing this user’s public key can obtain the certificate and verify that it is valid by way of the attached trusted signature.
X.509 Certificates|X.509 证书
X.509 定义了一个框架,用于通过目录为用户提供认证服务。X.509 defines a framework for providing authentication services to users via a directory.
该目录可以用作公钥证书的存储库。The directory may serve as a repository of public-key certificates.
X.509 标准不指定使用特定算法,但推荐使用 RSA 算法。The X.509 standard does not dictate a specific algorithm but recommends RSA.
X.509 证书的一个重要特点是可以用于验证用户身份。An important feature of X.509 certificates is that they can be used to verify a user's identity.
Obtaining a User’s Certificate|获取用户证书
由 CA 生成的用户证书具有以下特点:
User certificates generated by a CA have the following characteristics:
任何拥有 CA 公钥的人都可以验证用户公钥。
除非证书被修改,否则没有其他方可以修改证书。
由于证书是不可伪造的,它们可以无保护地存储在目录中。
Revocation of Certificates|证书撤销
每个证书都有有效期。Each certificate has a validity period.
如果用户的私钥可能被泄露,或者用户不再受 CA 认证,证书可以提前撤销。A certificate can be revoked before expiration for reasons such as compromised private keys or changes in the user's certification status.
